Extra added hard drives without partitions.
Installation:
SDA is the drive where the proxmox installation is running SDB is the new drive that will be added to the proxmox.
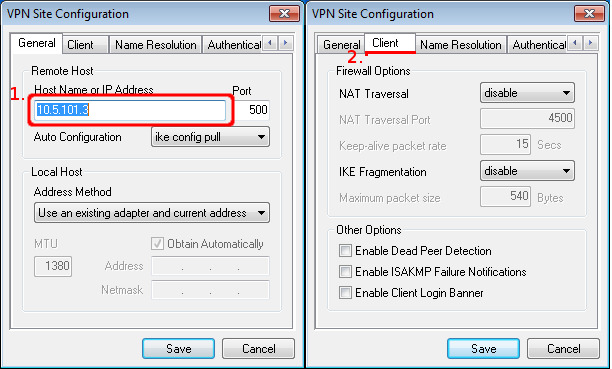
- Open the Proxmox Shell
With
fdisk you can find your drives that you want to add, if you are not
sure what the device name is for your hard drive that you want to add.
Type: fdisk -l
Type: fdisk -l
Find the "Disk" with no valid partition table. That will be probably your hard drive you want to add.
"Disk /dev/sdb doesn't contain a valid partition table"
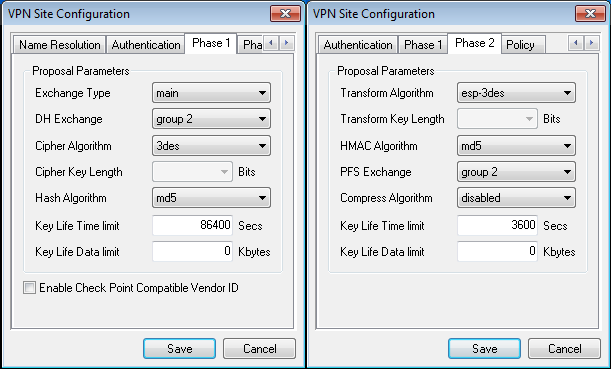
To make a partion on the new drive type the following:
Choose the following options:
New - Primary - Specify size in MB Write Quit
"Disk /dev/sdb doesn't contain a valid partition table"
To make a partion on the new drive type the following:
T - type cfdisk /dev/sdb
New - Primary - Specify size in MB Write Quit
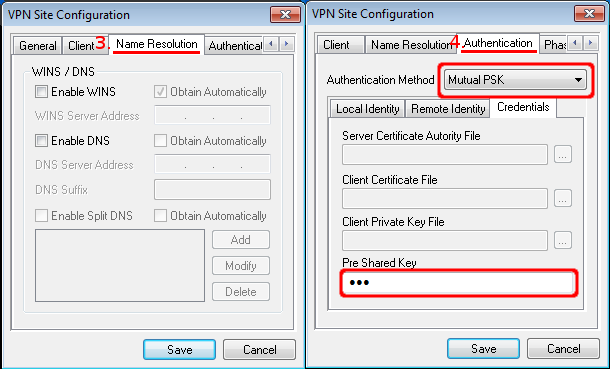
Now a physical volume has to be created.
- type pvcreate /dev/sdb1
- type pvcreate /dev/sdb1
Create
a volume group. The name "Data-Storage" is an example. You can name it
anyway you want. Consider a logical name, because this is the name that
will be used in the proxmox web interface:
Type: vgcreate Data-Storage /dev/sdb1
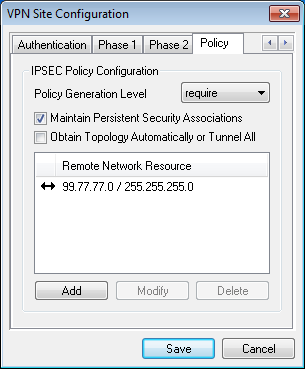
Add the storage in ProxMox
- In the webinterface click on the directory Datacenter and then click
on tab Storage.
on tab Storage.
- Click Add – LVM Group
o Type an ID Name for example data-storage
o Base Storage: Existing Volume Groups
o Volume Group: Data-Storage
o Enabled: Checked
o Other options should be adjusted accordenly to what you want
with it.
o Other options should be adjusted accordenly to what you want
with it.
Now the extra storage has been added in Proxmox and ready for use.
2. Mounting external HDD to be add to directory backup file
Startup the server and run the following from commandline to find the device name for the disk:
This should return something similar to this:
If it is the first new disk you have added it will more than likely be /dev/sdb as the device name.
Now we partition the disk:
Select the following options:
Mount the drive to a new folder:
Lastly we add the disk to /etc/fstab so it auto-mounts when we reboot the machine:
That’s your drive mounted and ready to be added as backup storage in Proxmox.
To test: reboot the machine and confirm that the drive is still mounted.
- fdisk -l
- Disk /dev/sda: 21.4 GB, 21474836480 bytes
- 255 heads, 63 sectors/track, 2610 cylinders
- Units = cylinders of 16065 * 512 = 8225280 bytes
- Device Boot Start End Blocks Id System
- /dev/sda1 * 1 2517 20217771 83 Linux
- /dev/sda2 2518 2610 747022+ 5 Extended
- /dev/sda5 2518 2610 746991 82 Linux swap / Solaris
- Disk /dev/sdb: 32.2 GB, 32212254720 bytes
- 255 heads, 63 sectors/track, 3916 cylinders
- Units = cylinders of 16065 * 512 = 8225280 bytes
- Disk /dev/sdb doesn't contain a valid partition table
Now we partition the disk:
- cfdisk /dev/sdb
- New > Primary > Enter (use the size in MB already specified)
- Write
- Quit
- mkfs.ext3 /dev/sdb1
- mkdir /mnt/backups
- mount -t ext3 /dev/sdb1 /mnt/backups
- /dev/sdb1 /mnt/backups ext3 defaults,errors=remount-ro 0 1
To test: reboot the machine and confirm that the drive is still mounted.